Cybersecurity for Media & Entertainment: Reducing risk in an evolving threat landscape


Improve threat intelligence and reduce risk in an ever-changing landscape.
Mitigating risks to assets and revenue begins with understanding a threat landscape that is constantly evolving. However today’s media companies are challenged by consequential decisions on a quarterly, and security solutions often slip out of prioritization.
High value content is the foundation of the media & entertainment industry. Those same content assets put the industry at high risk of data breach, as seen across entertainment organizations.
From post-production houses and video game companies to music labels and major motion picture studios, many media and entertainment (M&E) organizations need to enhance cybersecurity to better protect the content at the center of their business. To develop an effective strategy, these organizations must first understand current threats. They can then assess their current security posture and build cybersecurity solutions to close gaps now and in the future.
Cybersecurity for Media & Entertainment examines the security challenges that M&E faces as well as options for data protection and remediation.
Executive Summary
Mitigating risks to assets and revenue begins with understanding a threat landscape that is constantly evolving. However today’s media companies are challenged by consequential decisions on a quarterly, and security solutions often slip out of prioritization.
High value content is the foundation of the media & entertainment industry. Those same content assets put the industry at high risk of data breach, as seen across entertainment organizations.
From post-production houses and video game companies to music labels and major motion picture studios, many media and entertainment (M&E) organizations need to enhance cybersecurity to better protect the content at the center of their business. To develop an effective strategy, these organizations must first understand current threats. They can then assess their current security posture and build cybersecurity solutions to close gaps now and in the future.
Cybersecurity for Media & Entertainment examines the security challenges that M&E faces as well as options for data protection and remediation.
Your guide to cybersecurity for media and entertainment
Set the foundation for strengthening your security posture and protecting your most valuable assets.
For M&E companies, cybersecurity is rarely the highest priority. Organizations are focused on producing captivating content, expanding their audiences, addressing evolving consumer expectations, and developing new revenue streams.
But protecting intellectual property (IP), strategic plans, and other confidential data is critical. As previous breaches have shown, leaked content or the theft of sensitive information can directly impact revenues, lead to costly lawsuits and fines, and seriously damage a brand’s reputation. Many M&E companies need to strengthen cybersecurity to retain their competitive edge and avoid potentially devastating consequences.
Mergers and acquisitions among M&E companies amplify cybersecurity challenges. Attempting to fuse organizational structures, IT environments, and workforces can leave gaps that expose businesses to cyberattacks. In addition to integrating technologies, newly combined businesses need to coordinate security policies and processes to protect against both internal and external threats.
How can your organization best guard itself from cyberattacks? The first step is understanding the types of threats you face today. You can then pinpoint your unique vulnerabilities and begin addressing immediate needs. Next, you can start preparing for the future, anticipating the types of threats that could emerge as you adopt new technologies and expand into new ways of distributing content. A clear view of evolving threats and identification of gaps are essential for developing a robust cybersecurity plan—one that lets you stay focused on your core business objectives.
What are the aims of M&E cyberattacks?
While some cybercriminals want to disrupt the operations of large corporations or gain notoriety by breaking through particularly strong defenses, most M&E attackers are focused on stealing content and making money. They might steal content for their own purposes, sell pirated content, hold content for ransom, or commit fraud after pilfering sensitive information.
Piracy
Even years after many peer-to-peer content-sharing apps have been shut down, piracy is still a major problem for M&E companies. Piracy can involve any illegal downloading, unauthorized streaming, or other unlicensed access to M&E content.
According to a report from the U.S. Chamber of Commerce’s Global Innovation Center, global online piracy costs the U.S. economy approximately $29.2 billion in lost revenue each year.And piracy shows no real sign of slowing: Akamai found that between January and September of 2021, there were 3.7 billion unlicensed streams and downloads of movies, TV shows, and other content.
The Cost of Piracy
Many people who illegally download and stream content are doing so for their own personal entertainment—they might be using a borrowed or stolen password instead of subscribing to a streaming service. But there are also hackers who steal and re-sell content. No longer forced to sneak video recorders into movie theaters, hackers now have easier ways to capture streaming content and resell it over the internet.

Ransom
Some cybercriminals steal M&E content with the sole purpose of holding it for ransom. In 2017, a group of hackers stole episodes of the Netflix series Orange Is the New Black from a post-production studio and threatened to release the episodes unless a ransom was paid. Even after the post-production studio did pay a ransom, the hackers nevertheless released episodes online. Though Netflix did not disclose the financial damages caused by this particular attack, M&E organizations certainly stand to lose large sums in subscription fees or other revenues if content is released prematurely or illegally.
A ransomware attack—a slightly different tactic—can also cause significant financial damage. For example, if a hack prevents a studio from accessing its own work-in-progress content until a ransom is paid, that studio might be forced to pay or else start the painstaking process of recreating the work.
Infamous attacks on major studios
- 2014: Confidential information from Sony Pictures leaked and data erased.
- 2017: New episodes of Orange Is the New Black were held for ransom—then illegally released.
- 2017: HBO Hack of Game of Thrones
- 2022: The House of the Dragon script leak
Sensitive Information
In addition to protecting content and other IP, M&E companies must safeguard a wealth of private customer data and sensitive corporate information. Cybercriminals could gain hold of customers’ email addresses, passwords, phone numbers, or credit card numbers—and then sell that information to fraudsters. If hacks become public, M&E companies could suffer damaged reputations while also facing regulatory fines and becoming liable for customers’ financial losses.
Cybercriminals could also tap into confidential corporate information. In the Sony Pictures hack of 2014, cybercriminals not only accessed unreleased films and scripts, they also leaked personal information about Sony employees (including salary information), uncovered embarrassing employee emails, and exposed strategic plans. Hackers subsequently released malware that erased data.
How Do Cybercriminals Attack?
Cybercriminals draw from a large and growing array of tactics to infiltrate IT environments—but some are used much more frequently than others.
Social Engineering
Social engineering tactics, such as phishing, are by far the most common type of cybersecurity threats facing M&E businesses as well as companies in other industries. Social engineering uses human interactions to gain access to an organization’s systems or data.
With phishing, for example, an employee might receive an email that appears to be from a colleague or business partner. The email might ask the recipient to click on a link and then enter a username, reset a password, or provide other information. If the recipient complies, the hacker can then steal data (or money) from the recipient or use login credentials to gain wider access to corporate systems.
Phishing

Social engineering attacks such as phishing are the most common—and successful—types of attacks.
Social engineering attacks are prevalent because they work. Even tech-savvy employees can let their guard down and be fooled by seemingly authentic requests. For hackers, this approach provides a relatively simple way to break through cybersecurity defenses.
Ransomeware & Malware
Social engineering attacks give cybercriminals opportunities to inject ransomware or other malware into computer systems. Malware might enable hackers to steal data or automatically delete files. Ransomware uses encryption to block a company’s access to their own files until a ransom is paid, usually in cryptocurrency.
Ransomware is a key threat for M&E companies, whose content is among their most valuable assets. But M&E companies can also feel the impact of ransomware attacks when their businesses aren’t the direct targets. For example, in 2021, hackers attacked the workforce management services company Kronos, which supports 40 million people across 100 countries. More than 2,000 companies, in a range of fields, had difficulty tracking employee hours and issuing paychecks.
Distributed Denial of Service (DDoS) Attacks
M&E companies that deliver content through the internet can also be targets of distributed denial-of-service (DDoS) attacks, in which servers are flooded with internet traffic, preventing users from accessing websites or apps. The flood of traffic might originate from malware-infected company computers, mobile devices, or Internet of Things (IoT) devices.
M&E companies can also be affected by DDoS attacks on third parties: For example, if cloud service providers or DNS providers are attacked, those attacks can render online streaming services or other M&E sites inaccessible.
Error 404!
DDoS attacks can disable apps and websites, including those used for streaming services.

Zero-day Attacks
Zero-day attacks occur when hackers exploit a vulnerability in an application before developers can patch it. M&E companies—like businesses in other fields—can be subject to attacks through the software they use for everyday work. In addition, M&E companies that are building their own apps must be on heightened alert for vulnerabilities. Any vulnerabilities might expose their networks to attacks or jeopardize security of their customers’ devices.
Traffic Interception
Some cybercriminals attempt to intercept network traffic between systems. For example, a “man-in-the-middle” attack occurs when a hacker intercepts communication between a client (such as a laptop or mobile device) and a server. These types of attacks often use a public Wi-Fi network to intercept the traffic. The hacker might be able to capture usernames or passwords entered into apps or websites; the hacker can then use that information to infiltrate a company’s network.
How Can You Begin to Combat Cybercrime?
Developing an effective cybersecurity strategy begins with assessing your current state.
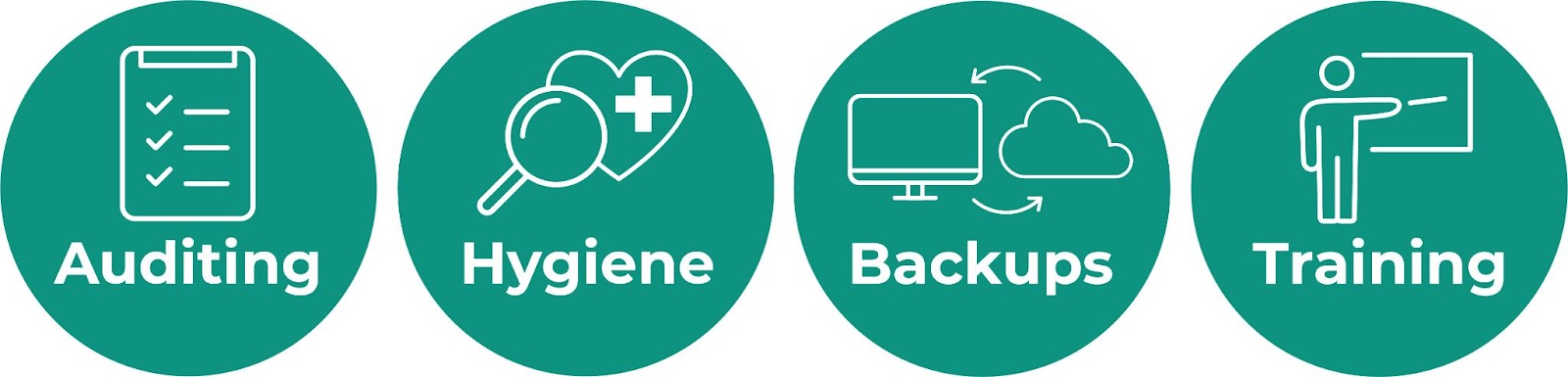
Conduct A Security Audit
For many organizations, the first step is conducting a thorough security audit. You need to fully understand your current security posture and evaluate your risks. External consultants can help generate a report card that assesses your company’s posture and risks against industry benchmarks.
If your business has recently merged with or acquired another business, your posture and risk profile may have changed. A merger or acquisition is a key moment to conduct an audit. A clear view of your current state and identification of gaps are critical for moving forward with business and IT integration.
Improve Cyber Hygiene
Once you’ve pinpointed potential gaps and vulnerabilities, you need to improve your cyber hygiene (or “digital” hygiene). That process can span everything from updating your infrastructure and improving network security to modifying workflows and training employees.
Assessing the technology that employees use is essential for reducing risks. Ensuring that operating systems and apps are up to date, employees are using strong passwords and multi-factor authentication, and remote workers are using VPNs can all help you prevent successful attacks.
Implement a Backup and Disaster Recovery Plan
You can minimize the impact of ransomware and other types of malware attacks with a robust backup and disaster recovery (DR) plan. If a hacker threatens to delete your files or permanently prevent you from accessing them, you can avoid having to pay a ransom if you have a reliable, recent backup of that data.
Of course, backup and DR plans also have the added benefit of protecting your content and important data from other types of losses. By regularly backing up data and keeping copies in geographically distant locations, you can help ensure your business will keep operating even if your primary data center experiences power outages, a fire, or a weather-related disaster.
Train Employees
To minimize the risk of social engineering attacks, your organization should train—and periodically retrain—your employees. Employees must understand the importance of avoiding social engineering schemes and know how to identify suspicious emails and texts. You should also have processes in place for reporting those suspicious messages so your IT and security groups can stop attacks from spreading.
The Future of Cybersecurity

Companies need to protect their employees—and businesses—however and wherever they connect with others.
5G
The emergence of 5G technology presents important opportunities for M&E companies. For example, you can use 5G to provide better connectivity to your distributed workforce. In addition, you can support more immersive, interactive experiences and enable customers to more easily stream content from anywhere.
But at the same time, 5G technology can create new risks. The shift away from centralized infrastructure and increasing use of edge environments, mobile devices, and IoT devices means that your organization must extend cybersecurity capabilities farther beyond the data center.
Virtual and Augmented Reality
Offering augmented reality apps or venturing into the metaverse can put your organization and your audience at risk of cyberattacks. Each new app, device, and environment gives hackers new opportunities to intercept network traffic, gain unauthorized access to data, and surreptitiously learn more about users. In particular, individuals participating in the metaverse place themselves at risk for social engineering schemes: A new friend in a virtual reality environment might be more interested in stealing passwords than forging a lasting relationship.
Planning for the future
Cybersecurity must be an ongoing effort. Cybercriminals continue to develop new types of attacks and modify their existing strategies. Meanwhile, M&E organizations continue to adopt new technologies that can inadvertently open new doors for hackers.
Start strengthening cybersecurity now
As cybercriminals continue to find new ways to steal content and illegally access other sensitive data, M&E businesses must make cybersecurity a high priority. Companies must better defend against the social engineering schemes, ransomware attacks, and other types of threats that can lead to lost revenues, regulatory fines, costly lawsuits, and damaged reputations.
For organizations undergoing mergers or acquisitions, auditing cybersecurity is crucial. These organizations need to avoid creating new security gaps as they integrate their businesses, IT environments, and workforces.
The Qvest cybersecurity consulting practice can help your organization address the complex landscape of cyberthreats facing the M&E industry. Our team draws on deep expertise, proven methodologies, strong partnerships, and an extensive understanding of leading security technologies. We can help you assess your current security posture, improve digital hygiene, implement the right technologies for your organization, and better prepare your employees for shifting threats.
Ready to learn more about how to protect your M&E organization? The Qvest Cybersecurity team is here to help.